Hi,
We’re using Azure AD provider and I’m trying to use OAuth to authenticate users on Indico through Azure AD.
Unfortunatly I haven’t succeeded so far:
Error message Login failed: No identity found
in Indico.log
Authentication via azure failed: No identity found (None)
Has anybody succeeded to authenticate through Azure AD, and if yes, can anyone tell me if I’m missing something?
_azure_oauth_config = {
'consumer_key': 'abcd', # put key here
'consumer_secret': '1234', # put secret here
'request_token_params': {'scope': 'User.Read'},
'request_token_url': None,
'access_token_method': 'POST',
'access_token_url': 'https://login.microsoftonline.com/{tenantid}/oauth2/v2.0/token',
'authorize_url': 'https://login.microsoftonline.com/{tenantid}/oauth2/v2.0/authorize'
# replace {tenantid} with the tenant id provided by Azure
}
AUTH_PROVIDERS = {
'azure': {
'type': 'oauth',
'title': 'Azure',
'oauth': _azure_oauth_config
}
}
IDENTITY_PROVIDERS = {
'azure': {
'type': 'oauth',
'oauth': _azure_oauth_config,
'endpoint': '/user',
'identifier_field': 'userPrincipalName',
> 'trusted_email': True,
> }
> }
How is that tenantid supposed to be guessed by Indico? I don’t think that will work (which maybe explains the issue?).
Hi,
Indeed, {tenantid} should be replaced by the tenant Id provided by azure.
I edited the code block for more clarity.
I actually tried to quickly configure login with Azure and it seems to work.
_azure_oauth_config = {
'access_token_method': 'POST',
'authorize_url': 'https://login.microsoftonline.com/common/oauth2/v2.0/authorize',
'access_token_url': 'https://login.microsoftonline.com/common/oauth2/v2.0/token',
'consumer_key': '----',
'consumer_secret': '----',
'request_token_url': None,
'request_token_params': {'scope': 'user.read'}
}
AUTH_PROVIDERS = {
"ms-azure": {
"type": "oauth",
"title": "Azure OAuth",
"oauth": _azure_oauth_config
}
}
IDENTITY_PROVIDERS = {
'ms-azure': {
'title': "Azure",
'trusted_email': True,
'type': 'oauth',
'oauth': _azure_oauth_config,
'endpoint': 'https://graph.microsoft.com/v1.0/me',
'identifier_field': 'id',
'mapping': {
'user_name': 'userPrincipalName',
'first_name': 'givenName',
'last_name': 'surname',
'phone': 'mobilePhone',
'email': 'mail'
}
}
}
PROVIDER_MAP = {"ms-azure": "ms-azure"}
The only problem seems to be that Azure doesn’t send back my e-mail address. I tried to play with the scope parameter to no avail. But at least this seems to solve your problem.
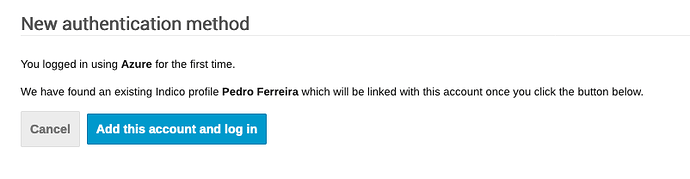
OK, if I try to do the same using my professional Azure account, it seems to work fine:
It does solve my problem !
Thanks for your help.