We have limited public IPs and many services are running with Apache proxy. We need to set up Indico on a separate system.
Can anyone give me a step by step guide on how to configure an external Apache proxy setup?
I am using this installation steps
https://docs.getindico.io/en/stable/installation/production/deb/apache/
I have try setting USE_PROXY = True in indico.conf
https://docs.getindico.io/en/stable/config/settings/#USE_PROXY
with this doc. I have added following conf in my apache conf.
...
RequestHeader set X-Forwarded-Proto expr=%{REQUEST_SCHEME}
RequestHeader set X-Forwarded-For %{REMOTE_ADDR}e
...
but doesn’t work
It’s batter to give external apache conf.
define “doesn’t work”…
@ThiefMaster Thank you for your quick response.
I have installed with apache proxy.
after I add system host entry like
192.168.100.1 indico.mydomain.com
reference: How to add a static entry in the ETC/host files
it’s working fine
after that I set my proxy (which link with Live IP).
this is my apache conf
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName indico.mydomain.com
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
# Options FollowSymLinks
# AllowOverride All
RewriteEngine On
<Location />
Require all granted
ProxyPass http://192.168.100.1/ timeout=1200
ProxyPassReverse http://192.168.100.1/
RequestHeader set X-Forwarded-Proto expr=%{REQUEST_SCHEME}
RequestHeader set X-Forwarded-For %{REMOTE_ADDR}e
</Location>
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
SSLCertificateFile /etc/letsencrypt/live/indico.mydomain.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/indico.mydomain.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>
</IfModule>
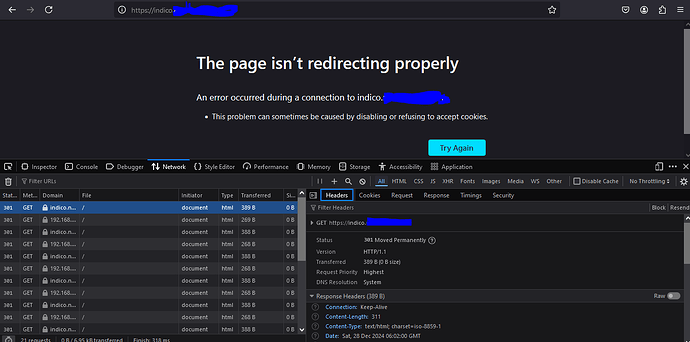
at this point I got this in browser
in my case workflow like this
Client ↔ HTTPS ↔ Apache Reverse Proxy ↔ HTTP ↔ Apache Indico
I have one public ip and use nginx proxy manager for multiple apps. That’s easy and the web interface is clear. All I have done is to forward all the external traffic to the ip address of the nginx proxy manager container.
Try passing the host header so it matches the host via which Indico is accessed. And on the nginx that’s running Indico, use that in the virtual host. And disable the forced https redirect, since you terminate TLS on your loadbalancer level.
I guess there is a space missing, it should be
<Location / >
Other things to check:
indico.conf:
base url = 'https://
nginx:
location / {
set_real_ip_from <your proxy>;
real_ip_header X-Forwarded-For;
....
Thanks @ThiefMaster @bpedersen2 @DeMiro5001 for your valuable replay
We can not move apache to nginx because 20+ service running in production.
with indico nginx setup (nginx — Indico 3.3.5 documentation)
I have skip step number 4 because I will handle TLS Certificate from my apache proxy. and also not required step 9.
Added USE_PROXY = True to indico.conf
echo -e "\nUSE_PROXY = True" >> ~/etc/indico.conf
@ThiefMaster Based on your suggestion I have made the following changes to the indico nginx conf.
and also I have changed port
/etc/nginx/conf.d/indico.conf
listen 8000;
listen [::]:8000;
server_name 192.168.100.1; # This is indico system IP. it doesn't matter. Write any host name.
# Redirect HTTPS to HTTP (optional, if requests might come via HTTPS)
if ($scheme = https) {
return 301 http://$server_name$request_uri;
}
access_log /opt/indico/log/nginx/access.log combined;
error_log /opt/indico/log/nginx/error.log;
if ($host != $server_name) {
rewrite ^/(.*) http://$server_name/$1 permanent;
}
location /.xsf/indico/ {
internal;
alias /opt/indico/;
}
location ~ ^/(images|fonts)(.*)/(.+?)(__v[0-9a-f]+)?\.([^.]+)$ {
alias /opt/indico/web/static/$1$2/$3.$5;
access_log off;
}
location ~ ^/(css|dist|images|fonts)/(.*)$ {
alias /opt/indico/web/static/$1/$2;
access_log off;
}
location /robots.txt {
alias /opt/indico/web/static/robots.txt;
access_log off;
}
location / {
root /var/empty/nginx;
include /etc/nginx/uwsgi_params;
uwsgi_pass unix:/opt/indico/web/uwsgi.sock;
uwsgi_param UWSGI_SCHEME $scheme;
uwsgi_read_timeout 15m;
uwsgi_buffers 32 32k;
uwsgi_busy_buffers_size 128k;
uwsgi_hide_header X-Sendfile;
client_max_body_size 1G;
}
at my apache proxy
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName indico.mydomain.com
RequestHeader set "X-Forwarded-Proto" expr=%{REQUEST_SCHEME}
RewriteEngine On
<Location />
Require all granted
ProxyPass http://192.168.100.1:8000/ timeout=1200
ProxyPassReverse http://192.168.100.1:8000/
RequestHeader set X-Forwarded-Proto expr=%{REQUEST_SCHEME}
RequestHeader set X-Forwarded-For %{REMOTE_ADDR}e
</Location>
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
SSLCertificateFile /etc/letsencrypt/live/indico.mydomain.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/indico.mydomain.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
</VirtualHost>
</IfModule>
NOW IT’S WORKING FINE.
Hop you modify the document accordingly so that it is easier for those who are setting up behind the proxy.